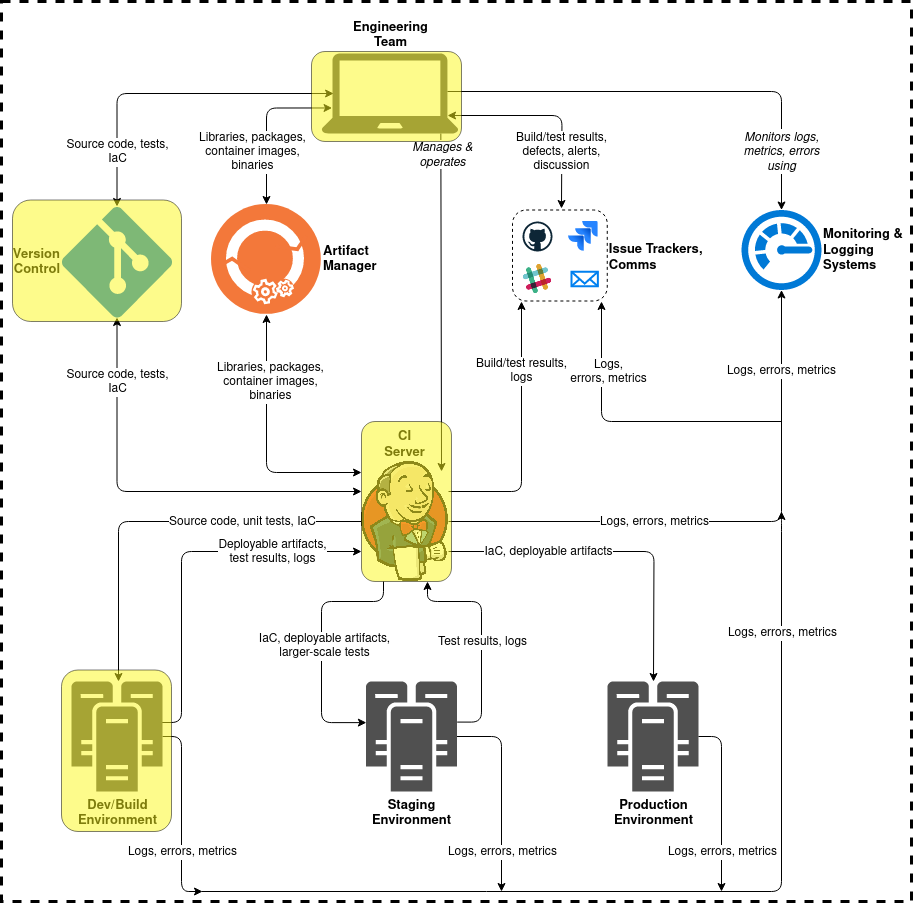
This post is part of a series on DevSecOps and CI/CD security. Check out the overview for context and links to the rest of the series.
This post explores using Git hooks for DevSecOps:
Git Hooks Overview
Git can run scripts in response to development events, providing a touchpoint to flag security issues. These are called git hooks, and they test a set of pass-fail conditions about a commit or codebase. If the tests fail, the hook fails with a non-zero exit status. This blocks the git action until the code is modified to pass the tests (or a developer overrides the hook).
If you’re new to git hooks, here’s some background information:
- Atlassian’s git hook tutorial: a hands-on guide to using git hooks
- Git hooks documentation: detailed information on the available Git hooks
Here’s where git hooks might run:
- From the command line or editor on the developer’s machine
- From the command line of a CI server or build environment
Git hooks are stored with the repository as specially-named scripts under .git/hooks/. For example:
- The
pre-commithook runs beforegit commitcompletes, and blocking the commit on a non-zero exit status. - The
pre-pushhook runs beforegit pushsends commits to a remote (GitHub, GitLab, etc.), blocking the push on a non-zero exit status.
Those are examples of client-side hooks that run on the developer’s machine or a CI server; there are also server-side hooks that run on the version control server.
Note that client-side hooks aren’t copied on git clone and can be easily overriden using git’s --no-verify flag, so if you’re trying to enforce security policies you want server-side hooks.
Git Hooks For Security
Here are some major security use cases for Git hooks:
- Triggering SAST and linters to flag security problems or violations of secure coding standards
- Triggering security unit tests
- Blocking commits containing secrets: API keys, AWS or cloud service provider keys, TLS/SSL private keys, passwords, SSH private keys, etc. This is a very common attack vector, to the point that GitHub proactively blocks commits containing known secret types.
Here are some pre-made security-oriented git hooks:
- git-secrets and gitleaks are open-source, regex-based tools with pre-commit hooks to prevent committing common secret types.
- OWASP Glue is a framework to run a series of security tools, designed to integrate at various points of software development. The project includes a container and a pre-commit hook to run the container. As of this writing the project’s latest commit was in December 2019, and it’s not “fire-and-forget”. Time investment in tool selection, tuning, and false positive filtering is needed to realize value.
The real power of git hooks lies in customizing them to your application and security needs.
Thanks for reading. If you like what you read, why not check out the next post in the series, covering security testing?